In the constantly evolving world of cryptocurrency, the security of funds remains a paramount concern for users. In the image below you can see a spectrum of cryptocurrency wallets categorized by their relative security and the associated risk of losing funds.
At the lower end of security, we find ‘custodial wallets’. These are wallets where the private keys are held by a third party, like a cryptocurrency exchange. While they offer convenience, the downside is a higher chance of losing funds due to the risk of the third party being hacked or acting maliciously.
Moving slightly up the security ladder are ‘hot wallets’. These are connected to the internet and include mobile and desktop wallets. They are more secure than custodial wallets because the user retains control over their private keys. However, being online, they are still vulnerable to hacks and malware.
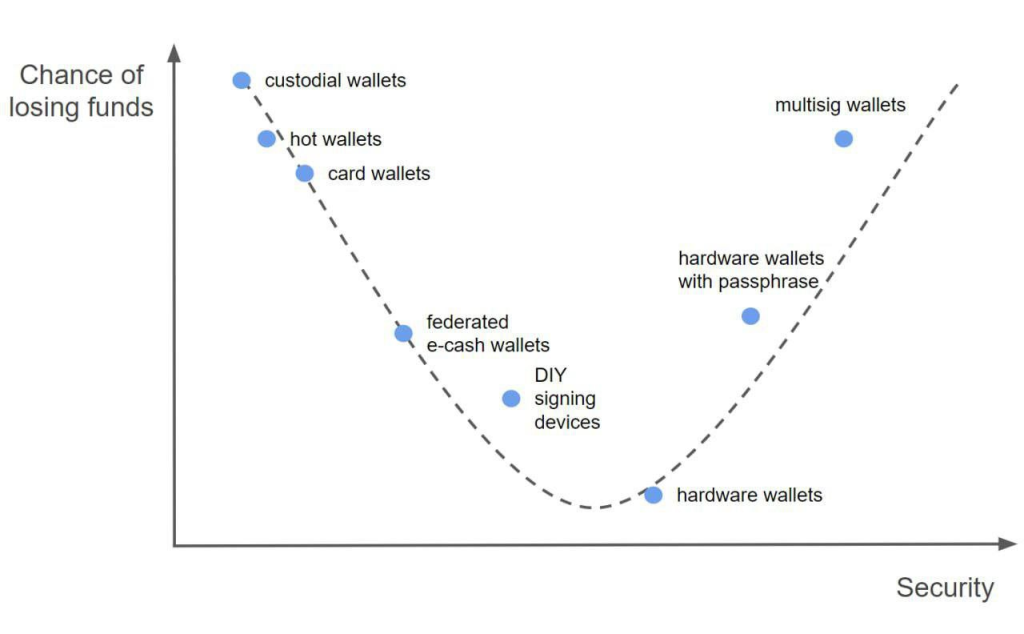
‘Card wallets’ are a form of cold storage, offering improved security by storing private keys on a physical card. However, if the card is lost or damaged, access to funds can be permanently lost.
In the middle of the spectrum, we encounter ‘federated wallets’ and ‘e-cash wallets’. Federated wallets are managed by multiple parties rather than a single entity, which can increase security through shared control. E-cash wallets, often used for digital cash systems, can offer anonymity and security but may still be susceptible to the failure of the underlying system.
‘DIY signing devices’ represent a unique approach where individuals create their own hardware wallets or use an air-gapped (never connected to the internet) computer to sign transactions. This method increases security but requires a higher level of technical expertise.
As we advance towards higher security, ‘hardware wallets’ are recommended for their ability to store private keys offline. They are widely regarded as a secure option for the storage of cryptocurrency assets, mitigating the risk of online vulnerabilities.
The highest security is attributed to ‘hardware wallets with a passphrase’. These devices require an additional passphrase, offering an extra layer of security on top of the already secure hardware wallet. If someone were to obtain the device, without the passphrase, the funds remain secure.
Lastly, ‘multisig wallets’ require multiple signatures to authorize a transaction. This spread of control across different entities or individuals significantly lowers the chance of losing funds due to unilateral actions or a single point of failure.
The graph emphasizes the trade-off between convenience and security in the choice of cryptocurrency wallets. Users must navigate this balance, considering their technical ability and the value of their holdings. It serves as a guide for those looking to secure their cryptocurrency investments, aligning their choices with their security needs and risk tolerance.
Author Profile

- Ex-community moderator of the Banano memecoin. I have since been involved with numerous cryptocurrencies, NFT projects and DeFi organizations. I write about crypto mainly.
Latest entries
- June 6, 2025NewsWireElon Musk to Decommission SpaceX Dragon after Trump Threat
- December 9, 2024Stock MarketMaster the Time Value of Money Financial Concept
- November 18, 2024Stock MarketFinancial Ratios Guide to Measuring Business Performance
- November 11, 2024NewsWireLabour’s UK Budget: A Fiscal Smirk of Contempt for Working People